Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Community Tip - Stay updated on what is happening on the PTC Community by subscribing to PTC Community Announcements. X
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Notify Moderator
OpenDJ as ThingWorx Directory Service with Docker
No ratings
OpenDJ is a directory server which is also the base for WindchillDS. It can be used for centralized user management and ThingWorx can be configured to login with users from this Directory Service.
Before we start
Pre-requisiste
- Docker on Ubuntu
- JKS keystore with a valid certificate
- JKS keystore is stored in /docker/certificates - on the machine that runs the Docker environments
- Certificate is generated with a Subject Alternative Name (SAN) extension for hostname, fully qualified hostname and IP address of the opendj (Docker) server
- Change the blue phrases to the correct passwords, machine names, etc. when following the instructions
- If possible, use a more secure password than "Password123456"... the one I use is really bad
Related Links
- https://hub.docker.com/r/openidentityplatform/opendj/
- https://backstage.forgerock.com/docs/opendj/2.6/admin-guide/#chap-change-certs
- https://backstage.forgerock.com/knowledge/kb/article/a43576900
Configuration
Generate the PKCS12 certificate
- Assume this is our working directory on the Docker machine (with the JKS certificate in it)
cd /docker/certificates
- Create .pin file containing the keystore password
echo "Password123456" > keystore.pin
- Convert existing JKS keystore into a new PKCS12 keystore
keytool -importkeystore -srcalias muc-twx-docker -destalias server-cert -srckeystore muc-twx-docker.jks -srcstoretype JKS -srcstorepass `cat keystore.pin` -destkeystore keystore -deststoretype PKCS12 -deststorepass `cat keystore.pin` -destkeypass `cat keystore.pin`
- Export keystore and Import into truststore
keytool -export -alias server-cert -keystore keystore -storepass `cat keystore.pin` -file server-cert.crt keytool -import -alias server-cert -keystore truststore -storepass `cat keystore.pin` -file server-cert.crt
Docker Image & Container
- Download and run
sudo docker pull openidentityplatform/opendj sudo docker run -d --name opendj --restart=always -p 389:1389 -p 636:1636 -p 4444:4444 -e BASE_DN=o=opendj -e ROOT_USER_DN=cn=Manager -e ROOT_PASSWORD=Password123456 -e SECRET_VOLUME=/var/secrets/opendj -v /docker/certificates:/var/secrets/opendj:ro openidentityplatform/opendj
- After building the container, it MUST be restarted immediately in order for recognizing the new certificates
sudo docker restart opendj
- Verify that the certificate is the correct one, execute on the machine that runs the Docker environments:
openssl s_client -connect localhost:636 -showcerts
Load the .ldif
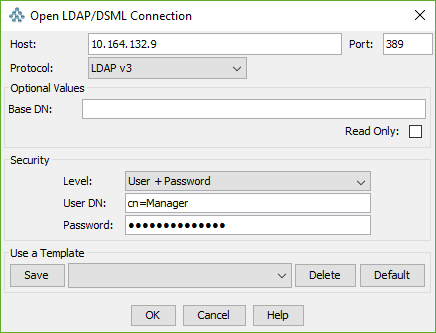
- Use e.g. JXplorer and connect
- Select the opendj node
- LDIF > Import File (my demo breakingbad.ldif is attached to this post)
- Skip any warnings and messages and continue to import the file
ThingWorx Tomcat
- If ThingWorx runs in Docker as well, a pre-defined keystore could be copied during image creation. Otherwise connect to the container via commandline:
sudo docker exec -it <ThingworxImageName> /bin/sh
- Tomcat configuration
cd /usr/local/openjdk-8/jre/lib/security openssl s_client -connect 10.164.132.9:636 -showcerts
- Copy the certifcate between BEGIN CERTIFACTE and END CERTIFICATE of above output into opendj.pem, e.g.
echo "<cert_goes_here>" > opendj.pem
- Import the certificate
keytool -keystore cacerts -import -alias opendj -file opendj.pem -storepass changeit
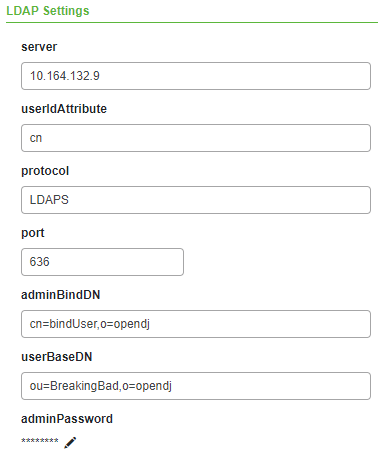
ThingWorx Composer
- As the IP address is used (the hostname is not mapped in Docker container) the certificate must have a SAN containing the IP address
- Only works with the TWLDAPExample Directory Service not the ADDS1, because ADDS1 uses hard coded Active Directory queries and structures and therefore does not work with OpenDJ.
- User ID (cn) must be pre-created in ThingWorx, so the user can login. There is no automatic user creation by the Directory Service.
- Make sure the Thing is Enabled under General Information
Appendix
LDAP Structure for breakingbad.ldif
- cn=Manager / Password123456
- All users with password Password123456