- Community
- IoT & Connectivity
- IoT & Connectivity Tips
- Securing MQTT connection to Thingworx platform
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Notify Moderator
Securing MQTT connection to Thingworx platform
Part I – Securing connection from remote device to Thingworx platform The goal of this first part is to setup a certificate authority (CA) and sign the certificates to authenticate MQTT clients. At the end of this first part the MQTT broker will only accept clients with a valid certificate. A note on terminology: TLS (Transport Layer Security) is the new name for SSL (Secure Sockets Layer). Requirements
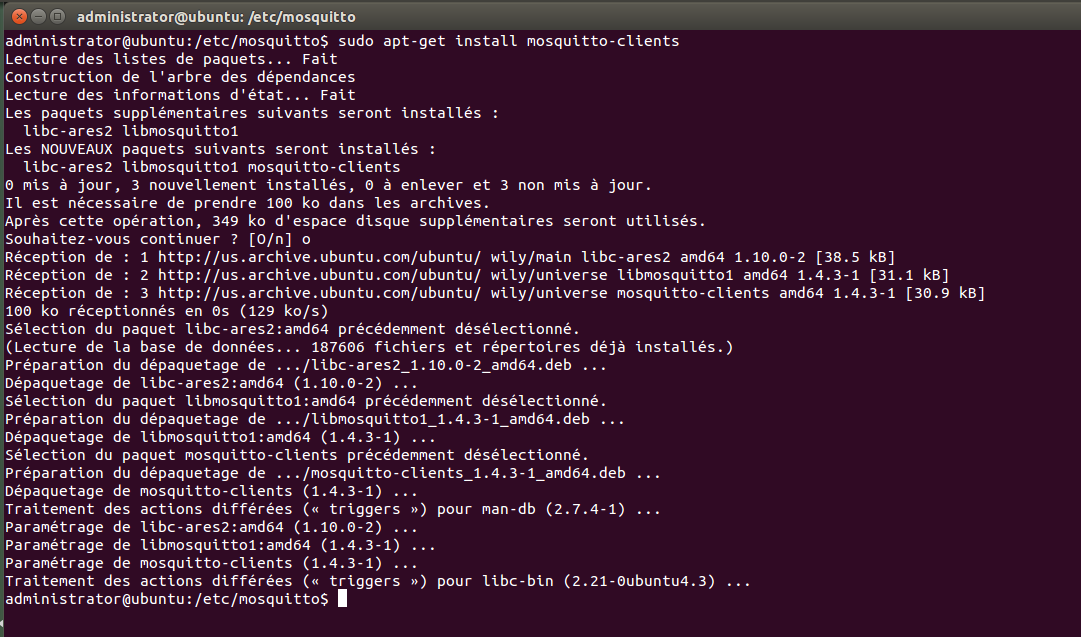
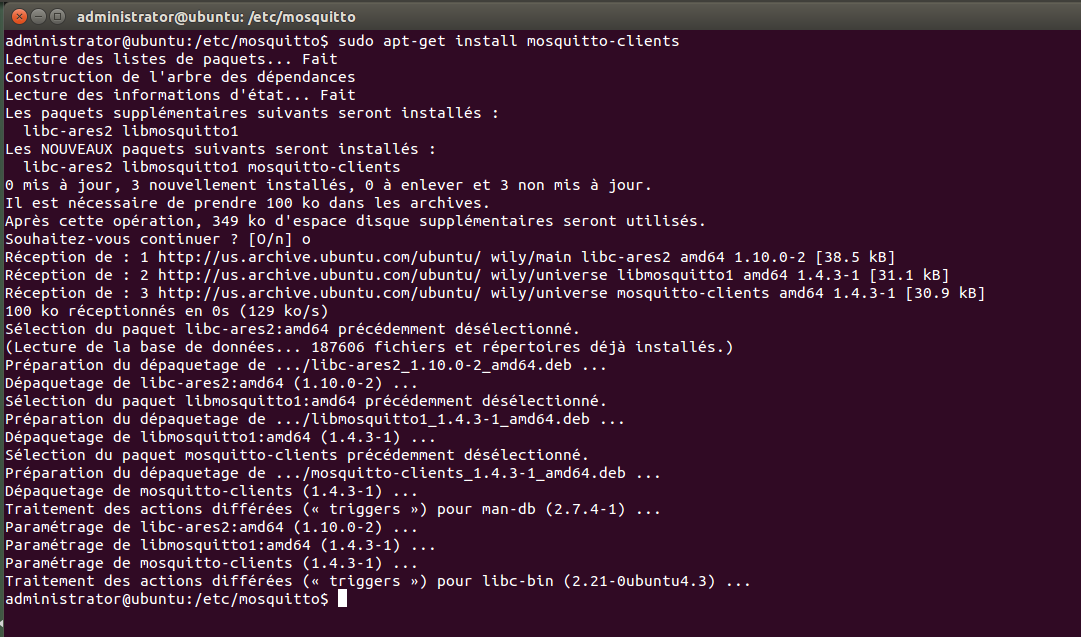
Demonstrations will be done with the open source MQTT broker, mosquitto. To install, use the apt-get command: $ sudo apt-get install mosquitto $ sudo apt-get install mosquitto-clients
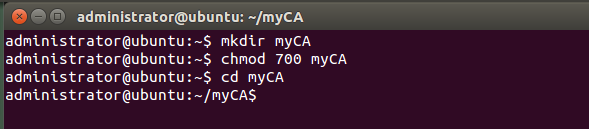
Procedure NOTE: This procedure assumes all the steps will be performed on the same system. 1. Setup a protected workspace Warning: the keys for the certificates are not protected with a password. $ mkdir myCA
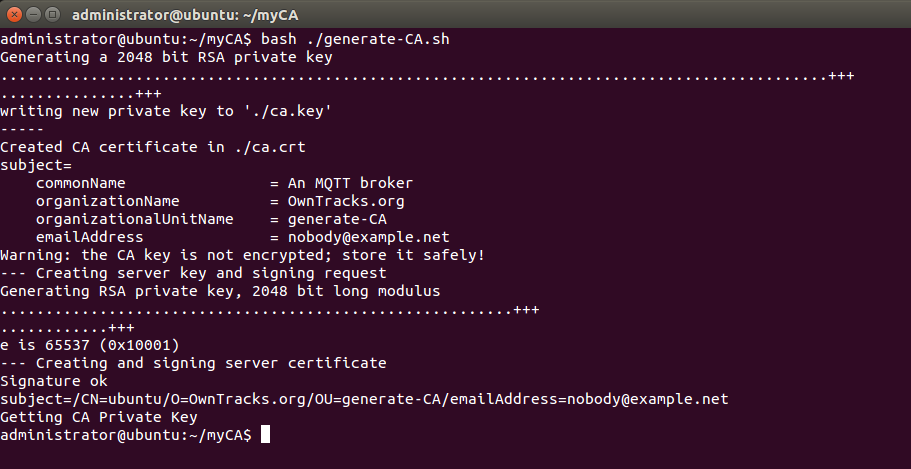
2. Setup a CA and generate the server certificates Download and run the generate-CA.sh script to create the certificate authority (CA) files, generate server certificates and use the CA to sign the certificates. NOTE: Open the script to customize it at your convenience. $ wget https://github.com/owntracks/tools/raw/master/TLS/generate-CA.sh . $ bash ./generate-CA.sh
The script produces six files: ca.crt, ca.key, ca.srl, myhost.crt, myhost.csr, and myhost.key. There are:
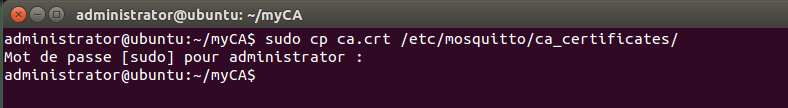
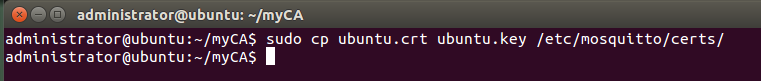
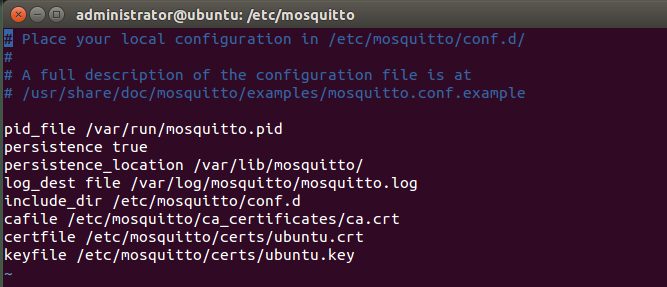
Note that the myhost files will have different names on your system (ubuntu in my case) Three of them get copied to the /etc/mosquitto/ directories: $ sudo cp ca.crt /etc/mosquitto/ca_certificates/ $ sudo cp myhost.crt myhost.key /etc/mosquitto/certs/ They are referenced in the /etc/mosquitto/mosquitto.conf file like this:
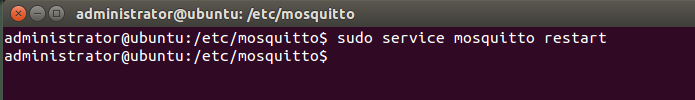
After copying the files and modifying the mosquitto.conf file, restart the server: $ sudo service mosquitto restart
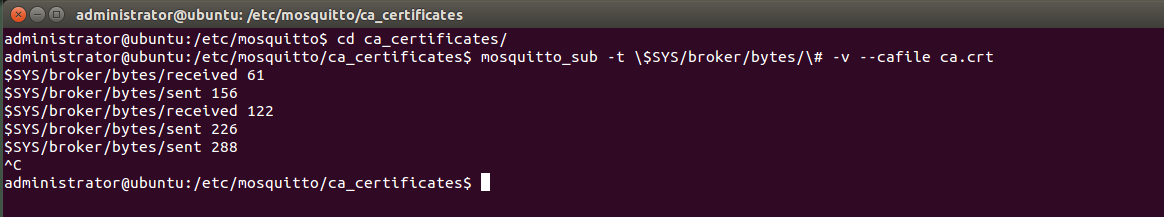
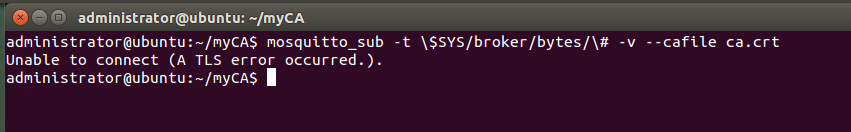
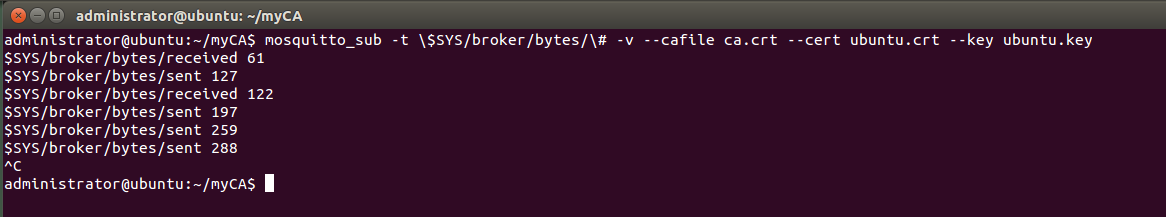
3. Checkpoint To validate the setup at this point, use mosquitto_sub client: If not already installed please install it: Change folder to ca_certificates and run the command : The topics are updated every 10 seconds. If debugging is needed you can add the -d flag to mosquitto_sub
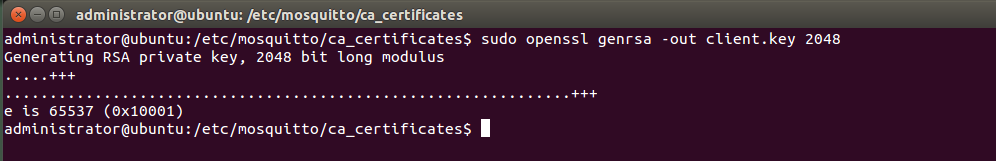
The following openssl commands would create the certificates: $ openssl genrsa -out client.key 2048
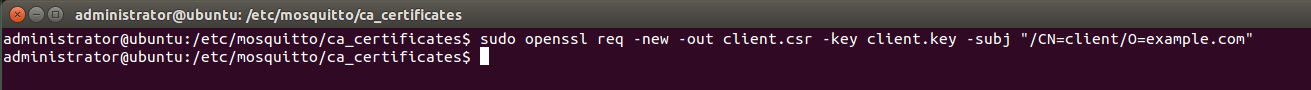
$ openssl req -new -out client.csr -key client.key -subj "/CN=client/O=example.com"
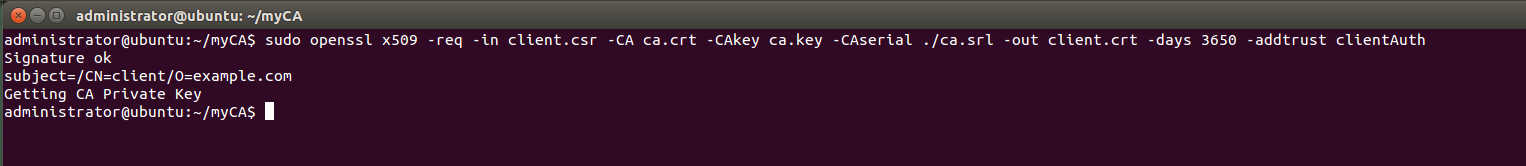
The argument -addtrust clientAuth makes the resulting signed certificate suitable for use with a client.
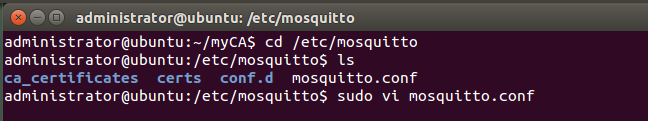
Change the mosquitto configuration file
To add the require_certificate line to the end of the /etc/mosquitto/mosquitto.conf file so that it looks like this:
Restart the server: $ sudo service mosquitto restart
6. Test The mosquitto_sub command we used above now fails:
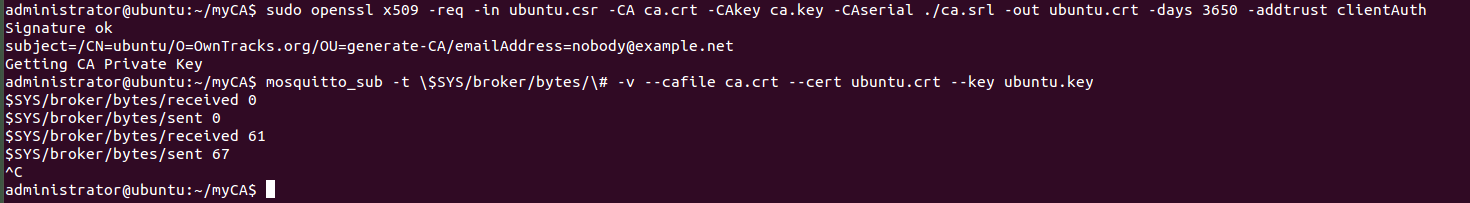
Adding the --cert and --key arguments satisfies the server: $ mosquitto_sub -t \$SYS/broker/bytes/\# -v --cafile ca.crt --cert client.crt --key client.key
To be able to obtain the corresponding certificates and key for my server (named ubuntu), use the following syntax:
And run the following command:
Conclusion This first part permit to establish a secure connection from a remote thing to the MQTT broker. |
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Notify Moderator
Hi,
this topic is very interesting for me.
Could you explain how to connect ThingWorx Core server and mosquitto server separately via X509 certificaiton?