Community Tip - Did you get an answer that solved your problem? Please mark it as an Accepted Solution so others with the same problem can find the answer easily. X
- Community
- PLM
- Windchill Discussions
- Re: ACL Issue
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ACL Issue
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify Moderator
ACL Issue
I am using Windchill PDMLink Release 12.0 and Datecode with CPS 12.0.2.7
Rehost from production server to Qualification server in order to validate some ACL functionality
Custom Role "PartDoc Author" in production is granted to create Part
Same Custom Role "PartDoc Author" in Qualification server does not have same behavior
When click or launch "Part creation" > Error is raised.
Here are the errors that I faced
Attention : Action Unavailable
You do not have create permission for this object. Please contact your system administrator.
- Labels:
-
Customization
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify Moderator
Hi,
Please check the ACL for the custom Role, there may be some "Deny" permission. Check MS logs.
Rgds
Hari
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify Moderator
Hi @Hari_Vara,
Thanks for your answer but we've made some check on policy administration and we do not found any "Deny" permission on "PartDoc Auhtor" Role.
See extract log from MS regarding ACL (no "Deny" permission) during Part creation process with user "rrakotov" member of this Role.
DEBUG [ajp-nio-127.0.0.1-8010-exec-3] wt.access.evaluation.policyACL rrakotov - => getPolicyAcl - IN: = wt.admin.AdministrativeDomain:6325995, wt.part.WTPart|1071177, INCREATION
DEBUG [ajp-nio-127.0.0.1-8010-exec-3] wt.access.evaluation.policyACL rrakotov - <= getPolicyAcl - OUT - acl from cache: wt.admin.AdministrativeDomain:6325995, wt.part.WTPart|1071177, INCREATION
DEBUG [ajp-nio-127.0.0.1-8010-exec-3] wt.access.evaluation.policyACL rrakotov - + Participant: Sharing Manager (Product - SLTE 1620 SOFTNODE) (wt.org.WTGroup:70576678): [Change Permissions]
DEBUG [ajp-nio-127.0.0.1-8010-exec-3] wt.access.evaluation.policyACL rrakotov - + Participant: Guest_Plus (Product - SLTE 1620 SOFTNODE) (wt.org.WTGroup:103050606): [Read, Download]
DEBUG [ajp-nio-127.0.0.1-8010-exec-3] wt.access.evaluation.policyACL rrakotov - + Participant: Product Manager (Product - SLTE 1620 SOFTNODE) (wt.org.WTGroup:6325996): [Full Control (All)]
DEBUG [ajp-nio-127.0.0.1-8010-exec-3] wt.access.evaluation.policyACL rrakotov - + Participant: Organization Administrator (ASN_Org) (wt.org.WTGroup:1061725): [Full Control (All)]
DEBUG [ajp-nio-127.0.0.1-8010-exec-3] wt.access.evaluation.policyACL rrakotov - + Participant: Team Members (Product - SLTE 1620 SOFTNODE) (wt.org.WTGroup:6325997): [Read, Download]
DEBUG [ajp-nio-127.0.0.1-8010-exec-3] wt.access.evaluation.policyACL rrakotov - + Participant: Supplier Administrators (ASN_Org) (wt.org.WTGroup:1061886): [Read]
DEBUG [ajp-nio-127.0.0.1-8010-exec-3] wt.access.evaluation.policyACL rrakotov - + Participant: Administrators (Site) (wt.org.WTGroup:15): [Full Control (All)]
DEBUG [ajp-nio-127.0.0.1-8010-exec-3] wt.access.evaluation.policyACL rrakotov - + Participant: Guest (Product - SLTE 1620 SOFTNODE) (wt.org.WTGroup:6327103): [Read, Download]
DEBUG [ajp-nio-127.0.0.1-8010-exec-3] wt.access.evaluation.policyACL rrakotov - ! Participant: Doc Author (Product - SLTE 1620 SOFTNODE) (wt.org.WTGroup:90687681): [Modify, Create, Delete, Administrative, Revise, New View Version, Change Permissions, Modify Content, Change Domain, Create By Move, Change Context, Set State, Modify Identity, Modify Security Labels]
DEBUG [ajp-nio-127.0.0.1-8010-exec-3] wt.access.evaluation.policyACL rrakotov - => getPolicyAcl - IN: = wt.admin.AdministrativeDomain:1061719, wt.pdmlink.PDMLinkProduct
DEBUG [ajp-nio-127.0.0.1-8010-exec-3] wt.access.evaluation.policyACL rrakotov - <= getPolicyAcl - OUT - acl from cache: wt.admin.AdministrativeDomain:1061719, wt.pdmlink.PDMLinkProduct
DEBUG [ajp-nio-127.0.0.1-8010-exec-3] wt.access.evaluation.policyACL rrakotov - + Participant: Product Creator (ASN_Org) (wt.org.WTGroup:1061729): [Create]
DEBUG [ajp-nio-127.0.0.1-8010-exec-3] wt.access.evaluation.policyACL rrakotov - + Participant: EMS - GROUP (ASN_Org) (wt.org.WTGroup:5436899): [Read]
DEBUG [ajp-nio-127.0.0.1-8010-exec-3] wt.access.evaluation.policyACL rrakotov - + Participant: Organization Administrator (ASN_Org) (wt.org.WTGroup:1061725): [Full Control (All)]
DEBUG [ajp-nio-127.0.0.1-8010-exec-3] wt.access.evaluation.policyACL rrakotov - + Participant: Administrators (Site) (wt.org.WTGroup:15): [Full Control (All)]
DEBUG [ajp-nio-127.0.0.1-8010-exec-3] wt.access.evaluation.policyACL rrakotov - => getPolicyAcl - IN: = wt.admin.AdministrativeDomain:6325995, wt.folder.SubFolder
DEBUG [ajp-nio-127.0.0.1-8010-exec-3] wt.access.evaluation.policyACL rrakotov - <= getPolicyAcl - OUT - acl from cache: wt.admin.AdministrativeDomain:6325995, wt.folder.SubFolder
DEBUG [ajp-nio-127.0.0.1-8010-exec-3] wt.access.evaluation.policyACL rrakotov - + Participant: Sharing Manager (Product - SLTE 1620 SOFTNODE) (wt.org.WTGroup:70576678): [Change Permissions]
DEBUG [ajp-nio-127.0.0.1-8010-exec-3] wt.access.evaluation.policyACL rrakotov - + Participant: Guest_Plus (Product - SLTE 1620 SOFTNODE) (wt.org.WTGroup:103050606): [Read, Download]
DEBUG [ajp-nio-127.0.0.1-8010-exec-3] wt.access.evaluation.policyACL rrakotov - + Participant: Product Manager (Product - SLTE 1620 SOFTNODE) (wt.org.WTGroup:6325996): [Full Control (All)]
DEBUG [ajp-nio-127.0.0.1-8010-exec-3] wt.access.evaluation.policyACL rrakotov - + Participant: Organization Administrator (ASN_Org) (wt.org.WTGroup:1061725): [Full Control (All)]
DEBUG [ajp-nio-127.0.0.1-8010-exec-3] wt.access.evaluation.policyACL rrakotov - + Participant: Team Members (Product - SLTE 1620 SOFTNODE) (wt.org.WTGroup:6325997): [Read, Modify, Modify Security Labels]
DEBUG [ajp-nio-127.0.0.1-8010-exec-3] wt.access.evaluation.policyACL rrakotov - + Participant: Administrators (Site) (wt.org.WTGroup:15): [Full Control (All)]
DEBUG [ajp-nio-127.0.0.1-8010-exec-3] wt.access.evaluation.policyACL rrakotov - + Participant: Guest (Product - SLTE 1620 SOFTNODE) (wt.org.WTGroup:6327103): [Read, Download]
DEBUG [ajp-nio-127.0.0.1-8010-exec-10] wt.access.evaluation.policyACL rrakotov - => getPolicyAcl - IN: = wt.admin.AdministrativeDomain:1061709, wt.org.WTOrganization
DEBUG [ajp-nio-127.0.0.1-8010-exec-10] wt.access.evaluation.policyACL rrakotov - <= getPolicyAcl - OUT - acl from cache: wt.admin.AdministrativeDomain:1061709, wt.org.WTOrganization
DEBUG [ajp-nio-127.0.0.1-8010-exec-10] wt.access.evaluation.policyACL rrakotov - + Participant: Unrestricted Organizations (Site) (wt.org.WTGroup:250): [Read]
DEBUG [ajp-nio-127.0.0.1-8010-exec-10] wt.access.evaluation.policyACL rrakotov - + Participant: All Participating Members (ASN_Org) (wt.org.WTGroup:1061754): [Read]
DEBUG [ajp-nio-127.0.0.1-8010-exec-10] wt.access.evaluation.policyACL rrakotov - + Participant: Unrestricted Supplier Administrators (Site) (wt.org.WTGroup:53453): [Create]
DEBUG [ajp-nio-127.0.0.1-8010-exec-10] wt.access.evaluation.policyACL rrakotov - + Participant: Organization Administrator (ASN_Org) (wt.org.WTGroup:1061725): [Full Control (All)]
DEBUG [ajp-nio-127.0.0.1-8010-exec-10] wt.access.evaluation.policyACL rrakotov - + Participant: Administrators (Site) (wt.org.WTGroup:15): [Full Control (All)]
DEBUG [ajp-nio-127.0.0.1-8010-exec-10] wt.access.evaluation.policyACL rrakotov - + Participant: ASN_Org (Site) (wt.org.WTOrganization:1061710): [Read]
DEBUG [ajp-nio-127.0.0.1-8010-exec-10] wt.access.evaluation.policyACL rrakotov - + Participant: Owner (Pseudo Role): [Full Control (All)]
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify Moderator
Logged on as admin, from an object (e.g. a Part), select Edit Access Control. This is not to edit / change the access but to investigate. It lists all sources of permissions here, allowing selection of groups / roles / individual users.
Best tool for investigating.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify Moderator
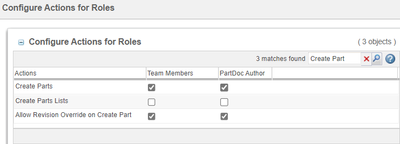
Actions on "PartDoc Author" role are set as-expected. -->
I will continue to investigate !
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify Moderator
Hello RRAKOTOV,
Did you check the MethodServer log when the issue occurs? Any relevant outputs?
KR,
Charles.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify Moderator
Hi @cgautier
nothing specific !!
I've already shared MS output when answering to @Hari_Vara.
I'll try to add a specific ACL for this role (in team members with right LC) and see if it will help to investigate.
Keep you in touch.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify Moderator
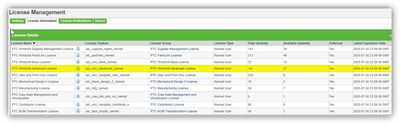
Check also the license applied to the test user.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify Moderator
Licensing is OK
--> "PTC Windchill advanced" is not fully used
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify Moderator
Have you tested in multiple Products/Libraries? Have you tested with multiple test users? Is it the same in all cases? A lot of times with access the easiest way is to find a case that works and then try to determine what is different between working case and non-working case.
There can be a lot to check for an access issue (and probably more than what I can think of):
- License(s) applied to the user
- Profile(s) applied to the user
- ACLs at the Org-level
- ACLs at the Product/Library level
- Role(s) that the user is in within the Product/Library
- "Configure Actions for Roles" set within the Product/Library
- folder-level Access Control (if set)
Also be sure to consider the type of part being created and the OIR for the part at the Org level and the Product/Library level. The ACL granting create must grant create for the type/subtype and correct state.
Also if you have any customizations, these can impact as well.